Virus
6:13 PM
How to Fix File folders become shortcuts or hidden in Removable media
Do you have Removable media, like Flash drives, SD memory cards, External HDD, that file folders become shortcuts or hidden? Don't reformat it yet. A virus or Trojan has infected your media device.
There are two methods on how we can fix this kind of problem.
Method 1
(Windows XP)
Open My Computer.- From the Tools menu, choose Folder Options
- Click on the View tab in the Folder Options window.
- In the Advanced settings: text area, locate the Hidden files and folders category.
- Choose the Show hidden files and folders radio button under the Hidden files and folders category.
- Click OK at the bottom of the Folder Options window.
(For Windows 7 and Windows 8)
 |
| Figure 1 |
- Click Organize see Figure 1
- Select Folder and search options see Figure 1
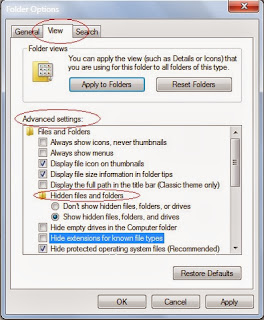
- Folder Options window will pop-up see Figure 2
- Click View tab
- In the Advanced settings: text area, locate the Hidden files and folders category.
- Choose the Show hidden files and folders radio button under the Hidden files and folders category.
- Unchecked : Hide empty drives in the computer folder, Hide extensions for known files
- Click OK at the bottom of the Folder Options window.
 |
| Figure 2 |
Method 2
Open Command Prompt
- Start > All Programs > Accessories see Figure 3
- Locate your Removable media or flash drive in My computer and remember what letter is assigned for your flash drive, it is usually G or F
- in the command prompt type in carefully Attrib -r -a -s -h /s /d G:\*.*
- the hit Enter key
note: replace G: with the letter of your flash drive.
note: replace G: with the letter of your flash drive.
This will show hidden files in your removable media, but this doesn't kill the virus or Trojan, be sure to scan your Flash drives with the updated AntiVirus like Avast, and Anti Malware software like Malwarebytes